Good practise suggests, that safeguarding the three most common ingress and egress routes (Email, Endpoint and the Web) places you in a good cyber security position. We address Web Security, and how SkyHigh provide solutions to protect the Users and Business from web risks, below is why you should have a Web Gateway Security solution:
-
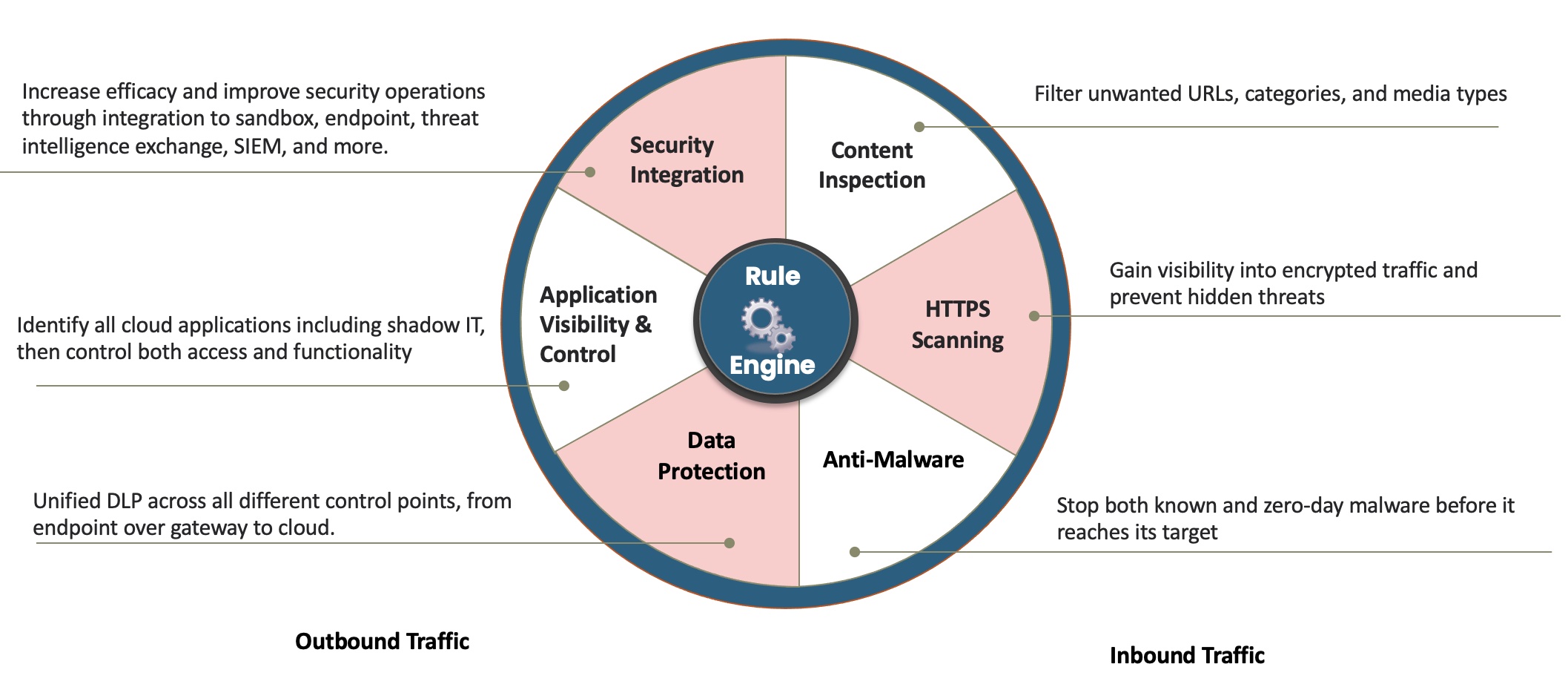
Threat Protection
- Examining web traffic for malware such as virus, trojans and ransomware prior to the threat reaching the Endpoint. NOTE: The ability to inspect encrypted web traffic is paramount with, as most web traffic now uses TLS encryption.
- Blocking access to fake “look-a-like” websites (where users may be deceived into sharing sensitive information and credentials), drive-by downloads, embedded links, and compromised legitimate sites.
- Mitigate potential threats through isolation, allowing users to still access sites for which there is no definitive verdict, without risk.
- Restrict, and in some cases even remove, exposure of Internal Resources to the Internet, while also applying more granular control over users’ access to said resources.
-
Compliance and Productivity
- Block access to web destinations prohibited by company policy, whether for compliance or productivity reasons.
- Manage access to everything else with granular controls to allow, coach, apply time restrictions, or grant users limited quotas of use.
-
Data Management
- Granularly control users’ access to cloud services, from allowing access to only approved services, to controlling what information can be stored on those services.
- Managing user access on a tenant-by-tenant basis in cloud services, ensuring company data is only ever uploaded to company-owned cloud service tenant, while still allowing read-only access to supplier/customer cloud service tenant.
- Manage public access to cloud-hosted data, even if uploaded prior to using Skyhigh or via out-of-band means. Scan cloud services for company data, assess it for sensitive data, and automatically remediate instances of excessive exposure or permissions.
- Examining web traffic for malware such as virus, trojans and ransomware prior to the threat reaching the Endpoint. NOTE: the ability to inspect encrypted web traffic is paramount with this task, as most web traffics now uses TLS encryption.
- Filtering undesirable or, nonproductive web sites. This is not just about managing what websites staff are permitted to visit (shopping, holidays, sport ………), but also preventing staff from inadvertently being directed to a fake “look-a-like” malicious website where they are deceived into sharing sensitive information such as logon credentials.
- Controlling blocked or permitted web Application. The Prevalence of cloud hosted applications and the lack of network visibility and native user access control can be problematic creating unintended data sharing risks.
- Preventing accidental or malicious data loss to the cloud. The ease of uploading information to the cloud makes for simple innocent mistakes or deliberate abuse.
Below is just one example of widely reported attack, the intention is to direct staff to a malicious web site.
Staff receive an email reportedly from their Administrator or from Microsoft, it is carefully crafted to mimic a genuine email. This email directs them to re-validate their o365 login credentials by logging into MS, the email presents an embedded URL and a compelling imperative styled message that if they do not respond quickly, they will lose access.
Unfortunately, the emails are counterfeits, and the link are not to Microsoft. Rather it’s the cyber criminals attempt to harvest the user’s login credentials, termed a Phishing attack. The attacks can quickly expand to ever more complex attacks, including requesting and intercepting OTP (one time pass) codes to bypass strong authentication controls. The Cybercriminal are continually trying to outwit the defences; Unfortunately, they just need to be successful once, whereas you need to be successful every single time. This is why Criminals broadcast so many attacks to as many users as possible, hoping there will be a single busy or distracted staff member who clicks on the bogus web link.
Key points about this attack:
- No actual payload/malware is delivered to the business, either in the email or from the bogus web page. Consequently, web download and email attachment scanning is of nil help here. We are not suggesting download & email file scanning are not beneficial, however relying on this for web threat protection alone affords a false sense of security.
- The objective is to steal staff credentials. The next step would be for the Criminals to gain access to the email account. Here they would typically email a similar message to all of the recipients from the User’s address-book, this to further increase the number of compromised accounts creating a ‘wider & larger impact’.
- Once in control of the email accounts, the Criminals will attempt extortion. This could be via creating email rule to identify keywords such as ‘invoice’, ‘payment’ or similar phrases suggesting financial topics. These same email rules can also divert email messages allowing the criminals to interfere and redirect payments to their bank accounts for instance. Or facilitating the Criminals to infiltrate the internal systems with ransomware where they seek payment to restore data or, mass harvesting email data and threatening to publish publicly.
Why SkyHIgh?
SkyHigh have three core solutions that form an integrated umbrella for web protection. These are typically delivered from the cloud, although uniquely they also have on-premises appliances. These together offers a centrally managed option for Network access, Web threat protection and Web Application control, a summary is below:
- ZTNA – (Zero Trust Networking Access) next generation technology VPN (Virtual Private Networking) to protect access to corporate networks.
- Robust centrally managed and seamless user experience to secure the access path to private corporate resources for remote and roaming staff.
- SWG - (Secure Web Gateway) for perimeter security.
- Safeguarding against internet malware with real-time download scanning, granular policy driven URL control, and sandboxing to isolate staff from web-based phishing attacks.
- CASB - (Cloud Access Security Broker) providing visibility and control of the staff interaction with Cloud applications.
- Securing access to Cloud applications and the usage i.e.: controlling file upload with permitted Cloud Apps whilst denying access to any non-approved Cloud Apps. Example: manage and securing AI tools (i.e., ChatGPT, Google Gemini, MS Copilot, Perplexity etc). The challenge being that staff want to utilise such AI tools for productivity improvements, however the business wants to control information sharing and intellectual property within such tools.
Please contact us to book a demonstration or request more information.
Secure Web Gateway
Enabling secure web connectivity for every device, user, and location.
Policy Incidents


